By default, the Data Flow server is unsecured and runs on an unencrypted HTTP connection. You can secure your REST endpoints,
as well as the Data Flow Dashboard by enabling HTTPS and requiring clients to authenticate.
For more details about securing the
REST endpoints and configuring to authenticate against an OAUTH backend (i.e: UAA/SSO running on Cloud Foundry), please
review the security section from the core reference guide. The security configurations can be configured in dataflow-server.yml or passed as environment variables through cf set-env commands.
Spring Cloud Data Flow can either integrate with Pivotal Single Sign-On Service (E.g. on PWS) or Cloud Foundry User Account and Authentication (UAA) Server.
When deploying Spring Cloud Data Flow to Cloud Foundry you can simply bind the application to the Pivotal Single Sign-On Service. By doing so, Spring Cloud Data Flow takes advantage of the Spring Cloud Single Sign-On Connector, which provides Cloud Foundry specific auto-configuration support for OAuth 2.0.
Simply bind the Pivotal Single Sign-On Service to your Data Flow Server app and Single Sign-On (SSO) via OAuth2 will be enabled by default.
Authorization is similarly support as for non-Cloud Foundry security scenarios. Please refer to the security section from the core Data Flow reference guide.
As the provisioning of roles can vary widely across environments, we assign by default all Spring Cloud Data Flow roles to users.
This can be customized by providing your own AuthoritiesExtractor.
One possible approach to set the custom AuthoritiesExtractor on the UserInfoTokenServices could be this:
public class MyUserInfoTokenServicesPostProcessor implements BeanPostProcessor { @Override public Object postProcessBeforeInitialization(Object bean, String beanName) { if (bean instanceof UserInfoTokenServices) { final UserInfoTokenServices userInfoTokenServices = (UserInfoTokenServices) bean; userInfoTokenServices.setAuthoritiesExtractor(ctx.getBean(AuthoritiesExtractor.class)); } return bean; } @Override public Object postProcessAfterInitialization(Object bean, String beanName) { return bean; } }
And you simply declare it in your configuration class:
@Bean public BeanPostProcessor myUserInfoTokenServicesPostProcessor() { BeanPostProcessor postProcessor = new MyUserInfoTokenServicesPostProcessor(); return postProcessor; }
The availability of this option depends on the used Cloud Foundry environment.
In order to provide UAA integration, you have to manually provide the necessary
OAuth2 configuration properties, for instance via the SPRING_APPLICATION_JSON
property.
{ "security.oauth2.client.client-id": "scdf", "security.oauth2.client.client-secret": "scdf-secret", "security.oauth2.client.access-token-uri": "https://login.cf.myhost.com/oauth/token", "security.oauth2.client.user-authorization-uri": "https://login.cf.myhost.com/oauth/authorize", "security.oauth2.resource.user-info-uri": "https://login.cf.myhost.com/userinfo" }
By default, the property spring.cloud.dataflow.security.cf-use-uaa is set to true. This property will activate a special
AuthoritiesExtractor CloudFoundryDataflowAuthoritiesExtractor.
If CloudFoundry UAA is not used, then make sure to set spring.cloud.dataflow.security.cf-use-uaa to false.
Under the covers this AuthoritiesExtractor will call out to the Cloud Foundry Apps API and ensure that users are in fact Space Developers.
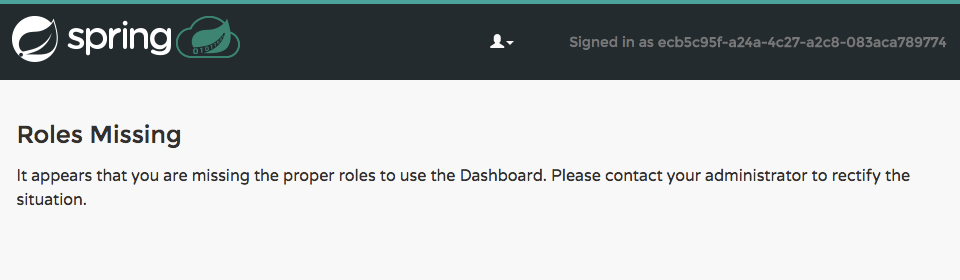
If the authenticated user is verified as Space Developer, all roles will be assigned, otherwise no roles whatsoever will be assigned. In that case you may see the following Dashboard screen: